Enabling single sign-on for your users must not be a big deal. There are multiple hybrid identity authentication scenarios available to obtain single sign-on capabilities to your users:
- Active Directory Federation Services (AD FS): single sign-on, based on one identity in your on-premises Active Directory and publishes on-premises and cloud web applications. This is the most complex scenario and often used by organizations with 250+ seats. They are not only using Office 365 applications for single sign-on, but also for other Intranet and Internet applications to achieve SSO user experience.
- Password Hash Sync (PHS): same sign-on, which means you must authenticate again with your on-premises credentials accessing Office 365 services.
- Pass-through authentication (PTA): single sign-on, allows your users to sign in to Azure Active Directory directly validating the users' passwords against your on-premises Active Directory.
- Seamless single sign-on: single sign-on, automatically signs your users in when they are on their corporate devices connected to your corporate network. Can be combined with either PHS or PTA.
When should I use AD FS instead of other hybrid authentication methods?
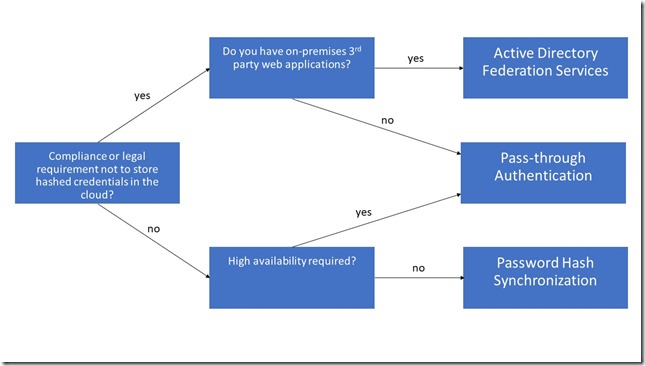
More information about the different sign in methods can be found in my edX course Manage Office 365 Identities.
Keep in mind that your AD FS deployment is essential for your users to access Office 365 applications. Both internal and external users require a stable running AD FS environment. Some basic considerations before starting the AD FS troubleshooting:
- Are your users having issues trying to connect within a corporate network or external?
- Try to exclude non-AD FS related issues like connection problems (VPN, ISP), wrong proxy settings, etc.
- Are your users using the correct credentials and authentication methods to connect? For example, correct UPN as user name, smart card authentication, third-party authentication providers like RSA, Windows Hello, etc.?
Here are some common and basic AD FS tests that can be performed:
As you can install and configure your AD FS farm with Azure AD Connect, you can also perform various AD FS-related tasks with minimal user intervention by using the AAD Connect wizard.
- Reset Azure AD and AD FS Trust
- Update AD FS SSL certificate
- Verify AD FS Login
If you are having sign-in issues, search for the Correlation ID or Activity ID, depending on the issue in your error message. For example:
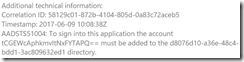
This ID is generated when the token issuance request comes to Federation Passive web application or directly to STS and remains the same for the entire duration of the request. Open the event viewer and have a look for this ID in the AD FS Admin log.
Another diagnostic tool from Microsoft is to use the Remote Connectivity Analyzer to verify the connectivity to your AD FS farm.
Finally, enable AD FS debug tracing:
- Open Event Viewer
- Right click Application and Services Logs and select View - Show Analytics and Debug Logs
- Navigate to AD FS Tracing, right click on Debug and select Enable Log to start debug tracing immediately.
I hope this little piece of information will help you to troubleshoot your federation services farm. Of course, there are a lot of more troubleshooting guides regarding AD FS available. These are only the basic tasks and how to identify the problem.