Delegate365 is using the Microsoft 365 and Azure standards to sign-in and to communicate with the Microsoft APIs. Here´s the best practice how to secure your environment for using Delegate365.
1. Secure your Microsoft 365 tenant
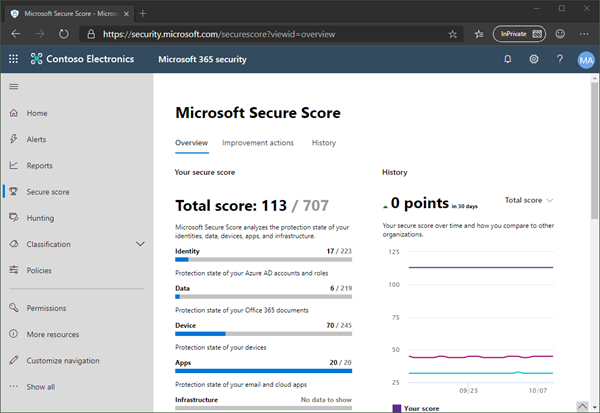
Microsoft 365 provides a bunch of features to harden a tenant and to raise the Secure Score. Every administrator should start improving the security with setting Conditional Access, MFA, and policies.
You can learn more about Microsoft Secure Score here. This demo tenant screenshot above is not properly configured and should definitely be secured. If your need support, we got you covered, see our Enterprise Security & Compliance Workshop offering.
2. Create a Service User for Delegate365
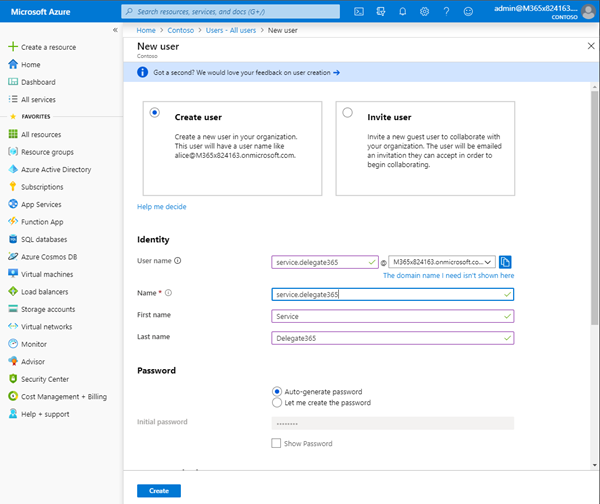
We recommend to create service users for specific purposes, such as for scheduled tasks, other apps and for Delegate365. Open the Azure portal and login as Global Admin. Navigate to Azure Active Directory - Users. Click on the New user link and create a service users, such as service.delegate365@yourcompany.com, similar as here.
Note the username and the password. We need these credentials for the sign-in process and to generate an app password later.
3. Assign the administrative role to the service account
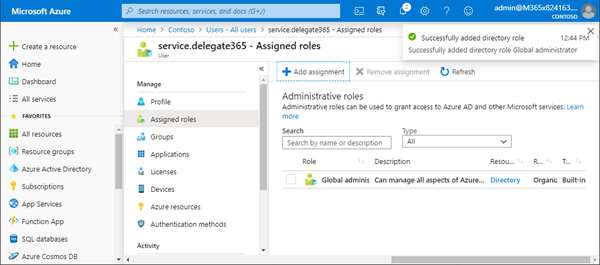
Open the newly created user from the Users list and assign the "Global Administrator" role to the service.delegate365 account. That user must be able to access the Azure Active Directory and to create the Delegate365 app. Click on the "Assigned roles" menu, then click on the "Add assignment" link. Search the "Global Administrator" role and click the Add button on the bottom. When done, the screen should look as here.
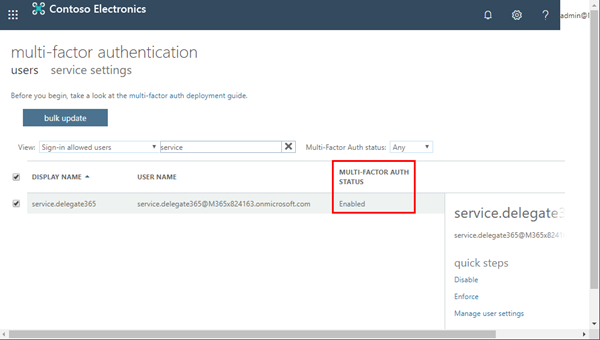
4. Ensure that MFA is not set for the service account (temporarily)
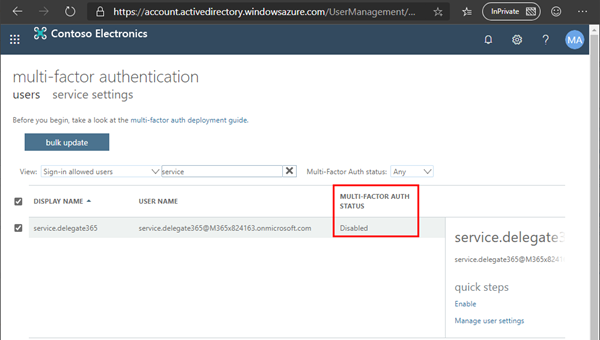
For the Delegate365 setup, we need a temporary Multi Factor Authentication (MFA) exception: MFA must be disabled for the service.delegate365 account. You can check that as Global Admin in the multi-factor authentication portal. Users themselves can use the https://aka.ms/MFASetup link to configure their second factor as needed anytime.
Note: After the Delegate365 setup, MFA should be activated again, see below. To setup MFA, see Set up multi-factor authentication.
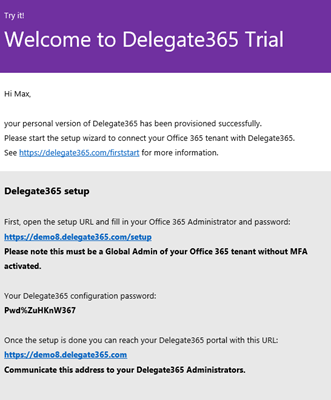
5. Run the Delegate365 setup
Now you need the data from your Delegate365 setup email: the setup URL and the Delegate365 configuration password. The subject title starts with "Welcome to Delegate365", the email looks as here:
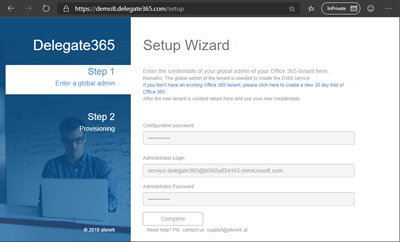
Open a browser in private mode, and open the setup URL. That´s the Delegate365 portal URL with /setup added. Enter the configuration password, the service.delegate365 account and the password.
The setup process will runs for one to two minutes. When completed, click on the Login button.
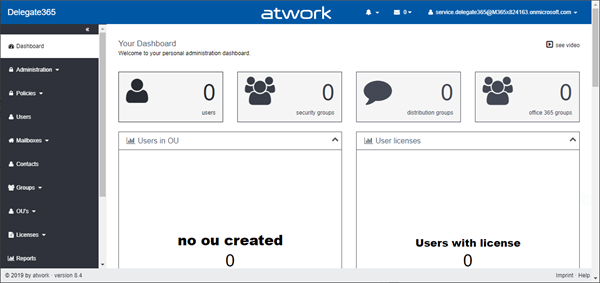
Sign-in with the service.delegate365 account. You will now see the Delegate365 dashboard.
You can start configuring Delegate365 now, or do that later. A box in the dashboard with links to the modules informs about the first steps such as creating OU´s and define Administrators. Also, check out the Delegate365 videos.
Leave that browser windows open, we will return in a minute.
6. (Re)Activate MFA for the service account
Open the multi-factor authentication portal as Global Admin and enable MFA for the service.delegate365 account as here.
See more about MFA at Set up multi-factor authentication.
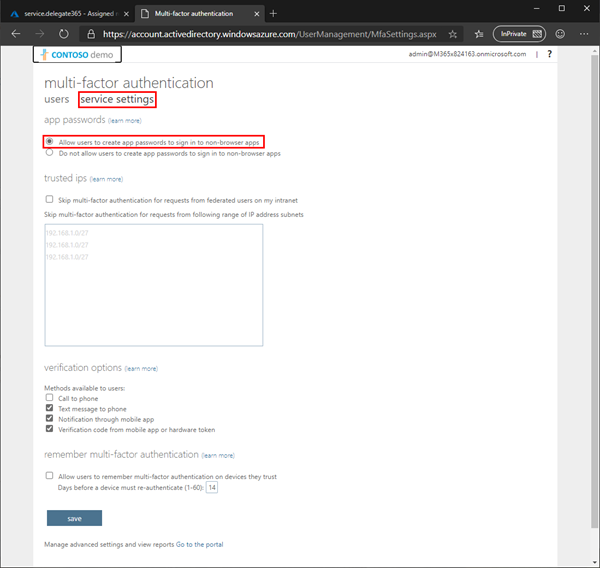
7. Enable App Passwords in your tenant
For client applications such as older versions of Outlook that cannot work with modern authentication methods, and for automation where there´s no second factor available such as in a scheduled unattended task, Microsoft provides "App passwords". These are automatically generated passwords that are harder for an attacker to guess and are more secure than a user password that is sent. Since Delegate365 is running as service, it requires to execute some Exchange operations without user interaction and without a second factor. This is, where the app password comes in for performing tasks automatically.
Open Multifactor settings portal as Global Admin. Open the "service settings" page and enable "Allow users to create app passwords to sign in to non-browser apps". Then, click the "Save" button at the bottom as here.
This enables app passwords in your tenant. Any user must then create his own app passwords if required. You can close that page then.
7. Setup MFA for the service account
Switch to the other browser where Delegate365 is still open and where you are signed-in as service.delegate365. Open another tab with the address of the multi-factor authentication portal. You should now be asked for the other factors for that account.
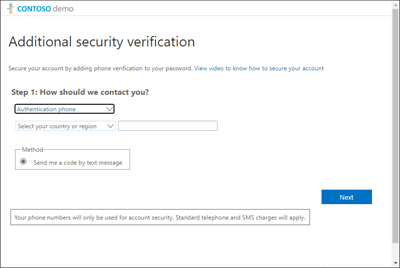
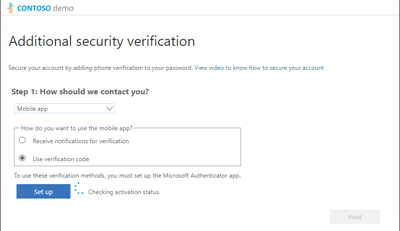
Configure the method you want use for the sign-in…
In most cases, the "Mobile App" is a good choice.
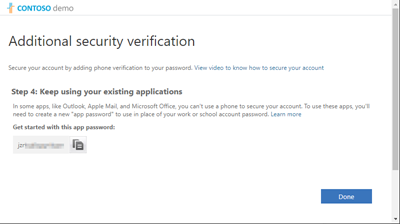
At the end, you will see a generated app password. We need that in Delegate365. Note that app password.
Here the app password is starting with "jzr…". Click "Done".
8. Get a new app password for accounts with MFA
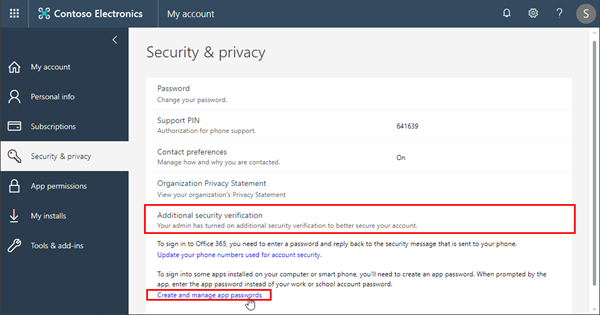
If you need to create an app password for an existing account with MFA enabled, login with that account and open the My Account website and follow the steps described at Create an app password for Office 365.
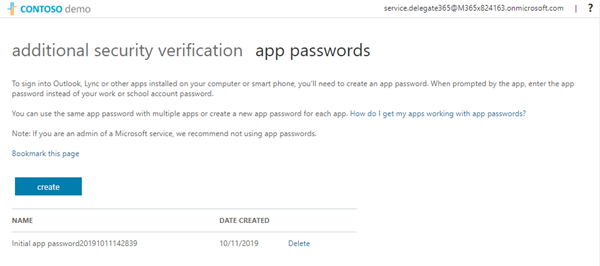
The link opens account.activedirectory.windowsazure.com/AppPasswords. Here, a user can manage his app passwords.
Microsoft recommends not to exceed 40 passwords and to use them per device, not only per app. Every user is responsible for his app passwords in the same way as for his user password.
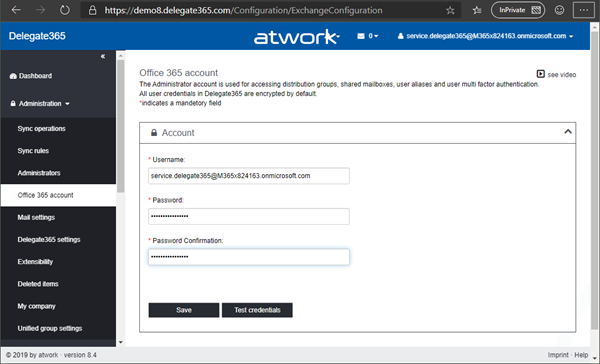
9. Use the service account and the app password in Delegate365
Now, when we have the app password created for the service.delegate365 account, we need to add the new credentials in Delegate365. Click on Administration / Office 365 account and enter the credentials of the service.delegate365 user and the app password (here it´s "jzr…"). Do not use the user password. Click on "Save".
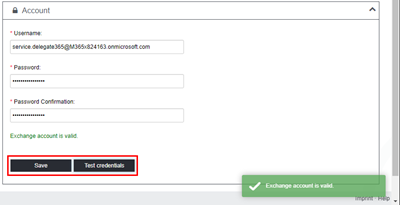
Then, click on the "Test credentials" button to see if the communication to Exchange Online works with the new credentials.
The message should inform that the Exchange account is valid. If the process fails, pls. check the service.delegate365 user credentials and create a new app password and use that for the service account.
Summary
We definitely recommend to use Secure Score and security settings such as Conditional Access and MFA to secure your Microsoft 365 environment. Delegate365 is using the same mechanism for user authentication as every other modern Microsoft services. For running specific Exchange operations, follow the steps above to create a service account and to use an app password to automate processes and to improve security.
Categories: Delegate365, Cloud, Azure, App, English, Microsoft365, Office365, Tools, atwork