In Delegate365, you can add any Microsoft 365 user as an external administrator. With this mechanism, users from other Microsoft 365 tenants can sign in to your organization’s Delegate365 as external users, without being connected to your own tenant. This article explains how this works, step by step.
Add an external user as an admin
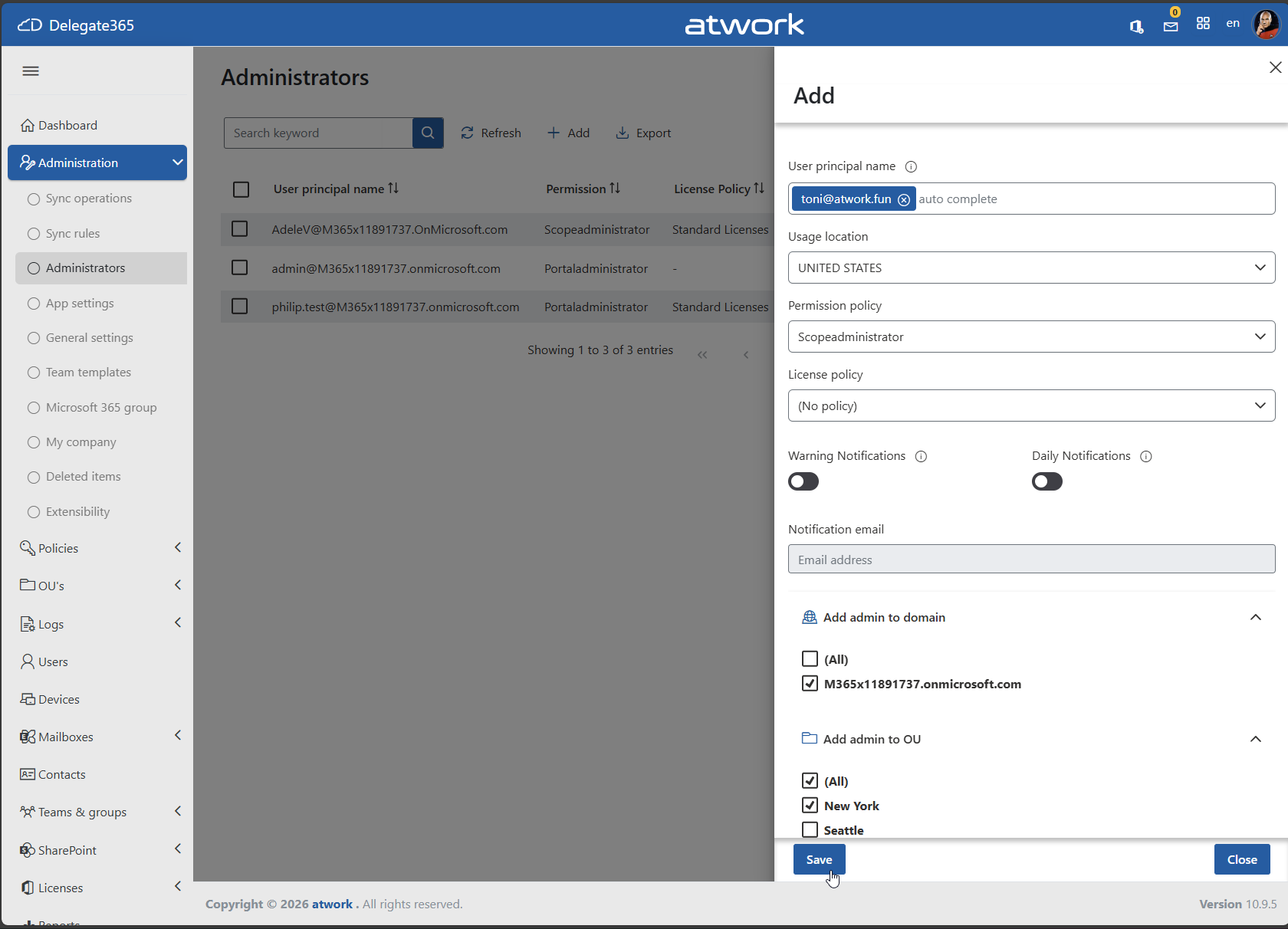
First, add the user as an administrator in the Delegate365 administrators list, as shown below.
In this example, the organization tenant is M365x11891737.onmicrosoft.com (the source tenant), and the external user is named admin5@atwork.fun. The user admin5 has a domain ending with atwork.fun, which belongs to an independent Microsoft 365 tenant (the target tenant).
External user opens Delegate365
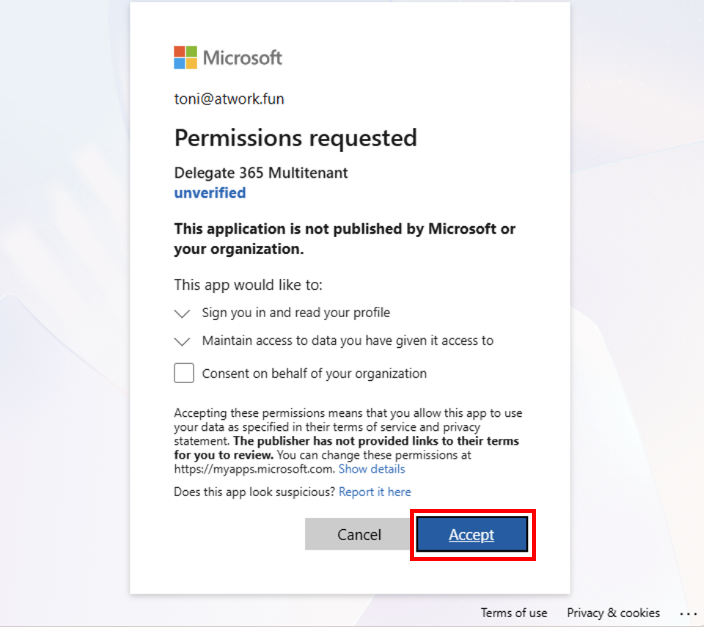
The external user opens the Delegate365 URL, for example https://someorganization.delegate365.com. On the first access, the Delegate365 app must be granted permission. The exact behavior depends on the Entra ID settings of the Microsoft 365 tenant.
Behavior depends on tenant settings
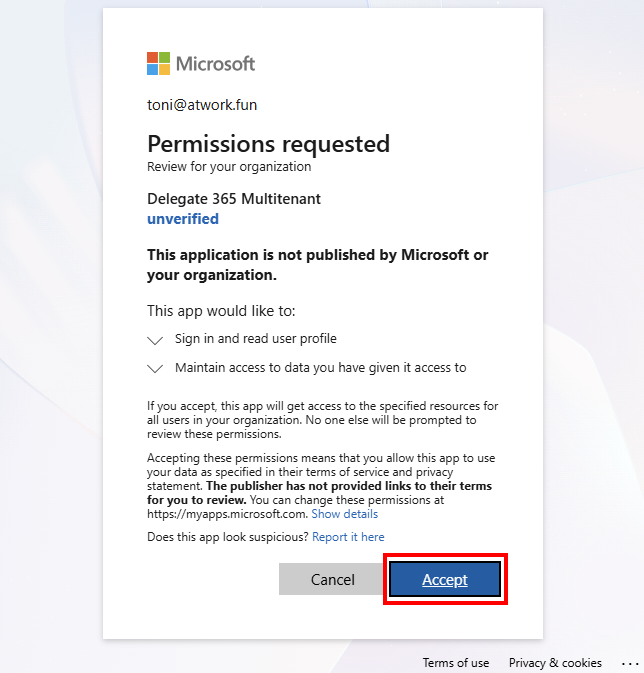
When the user opens the Delegate365 URL for the first time, the app consent screen appears, as shown below. In the best-case scenario, the user can simply click Accept, and Delegate365 opens.
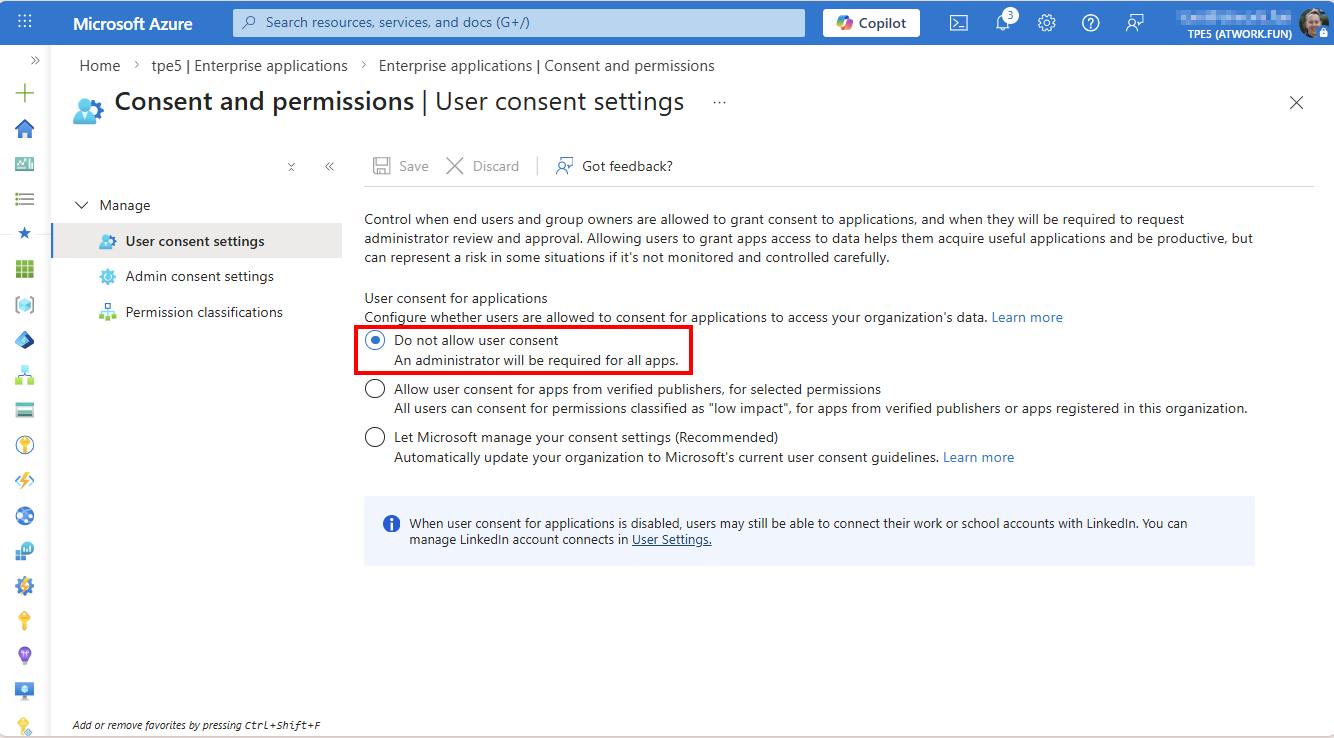
However, most organizations only allow administrators to grant app consent. This is typically configured as follows:
In Consent and permissions / User consent settings: Do not allow users consent:
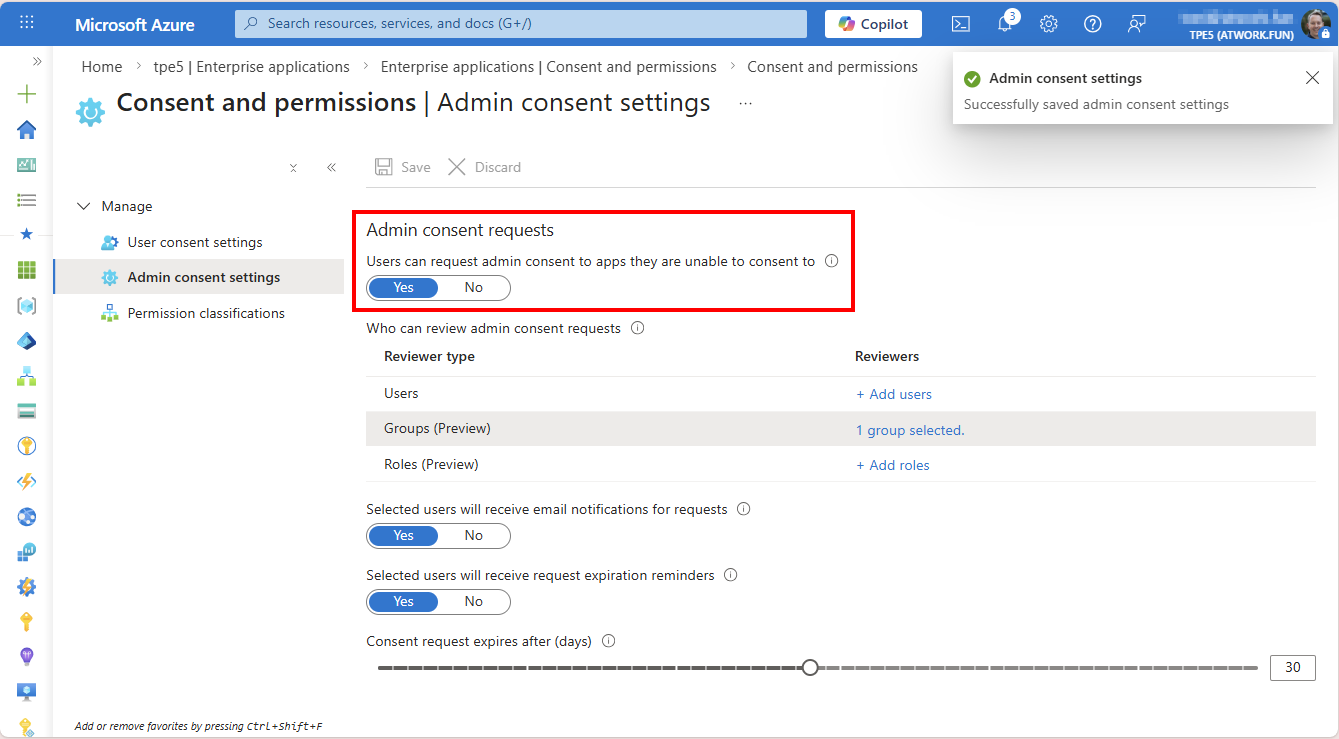
In Consent and permissions / Admins consent settings: Users can request admin consent to apps they are unable to consent to: Yes
With this configuration, an administrator of the Microsoft 365 tenant must grant consent on behalf of users and allow the Delegate365 multitenant app.
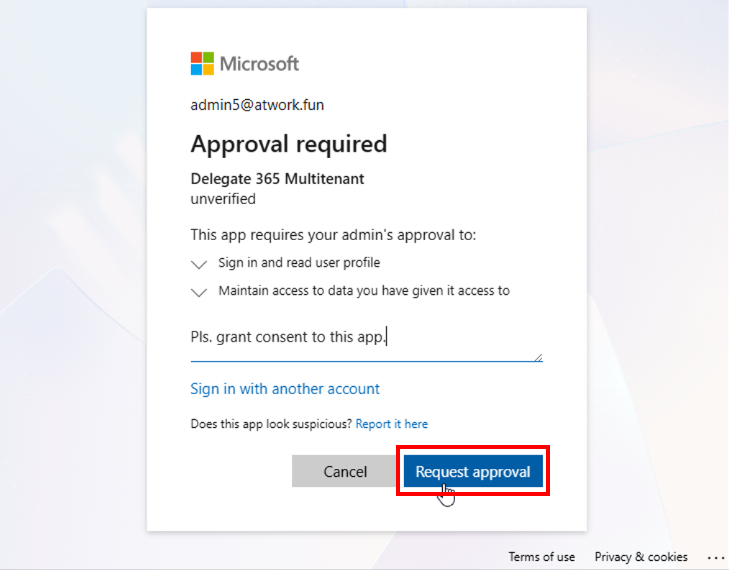
In this case, the user must request app permissions from an admin and provide a reason. Users can use the built‑in app permission request process and submit a request for approval, as shown here: Request approval:
Admin grants consent
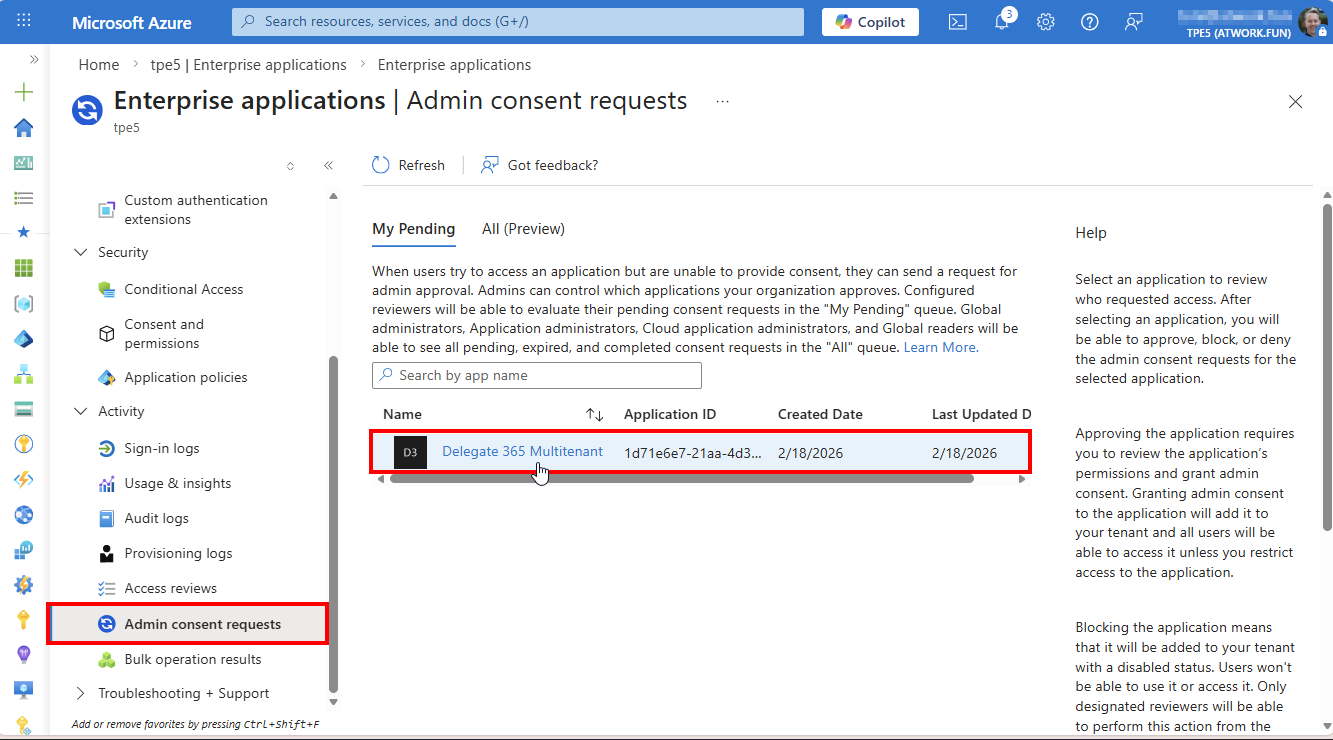
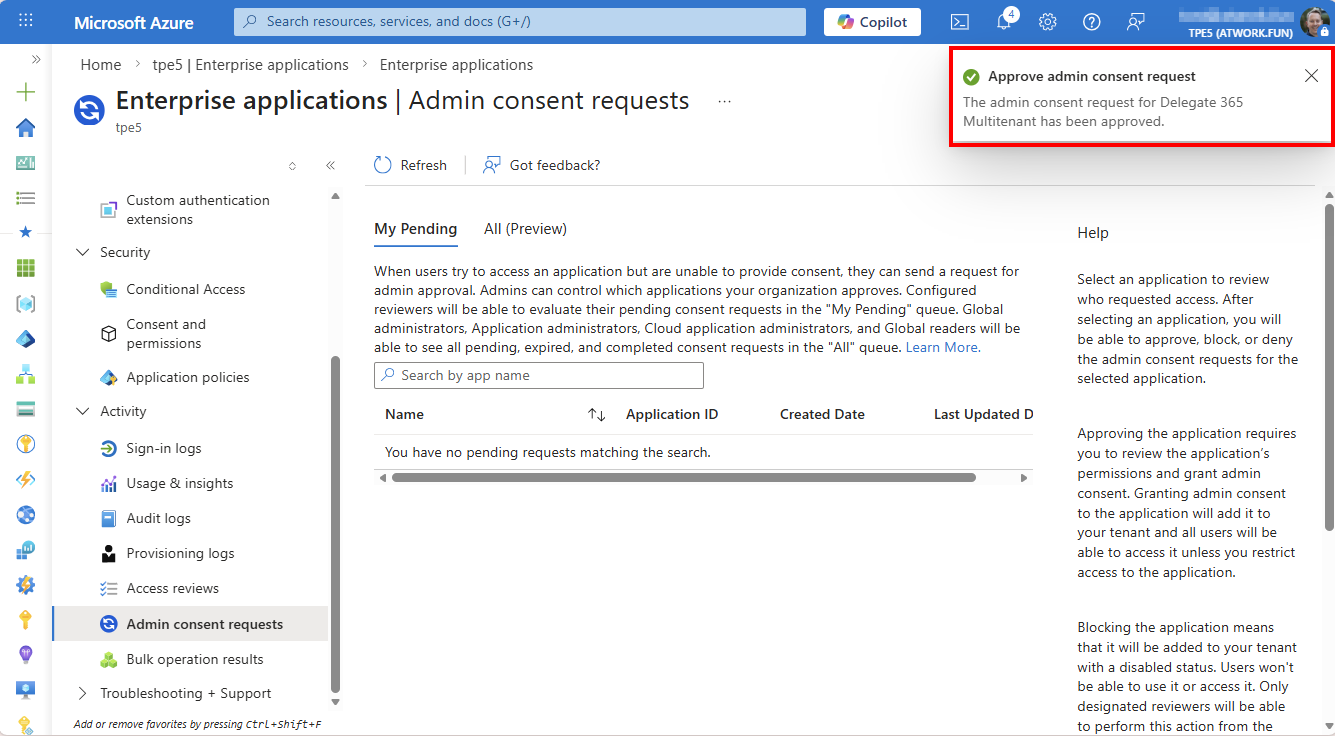
After the user submits the request, an administrator of the Microsoft 365 tenant must approve the app. The admin receives a notification and can grant access via Enterprise applications → Admin consent requests, as shown below.
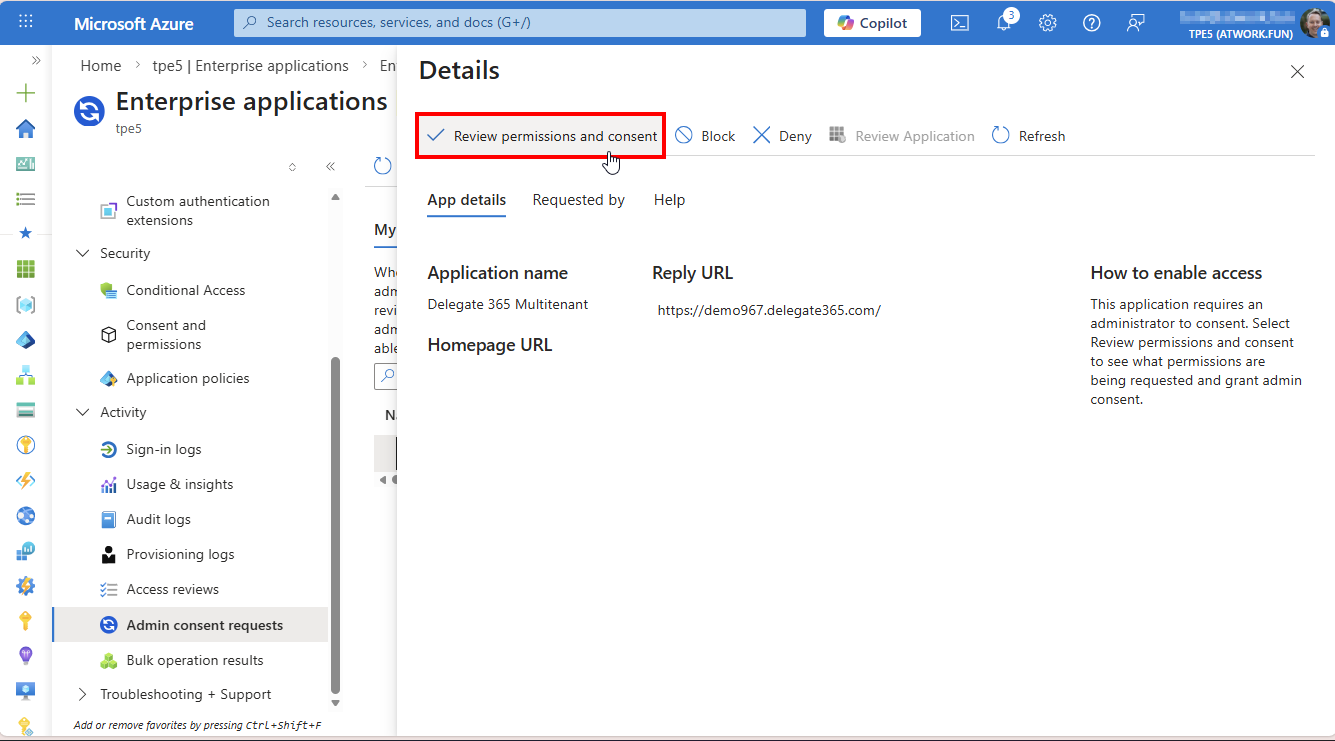
When the admin clicks the app name, the Details panel opens.
Here, the app can be approved using Review permissions and consent, or it can be blocked. The admin then consents to the app for all allowed users.
After confirmation, the request disappears and the app becomes available.
You can find more information about the Delegate365 app on the Delegate365 Applications page.
Users can use the app
When the app is confirmed, the user can retry opening the URL and sign in to the Delegate365 app successfully.
Summary
I hope this clarifies the responsibilities of the “remote” Microsoft 365 tenant. With this built‑in mechanism, users from other Microsoft 365 tenants can sign in and use Delegate365 as external administrators, while administrators retain full control and can allow or block the use of the Delegate365 app in their Microsoft 365 tenant.