Comparing Delegate365 Versions v9 vs. v10
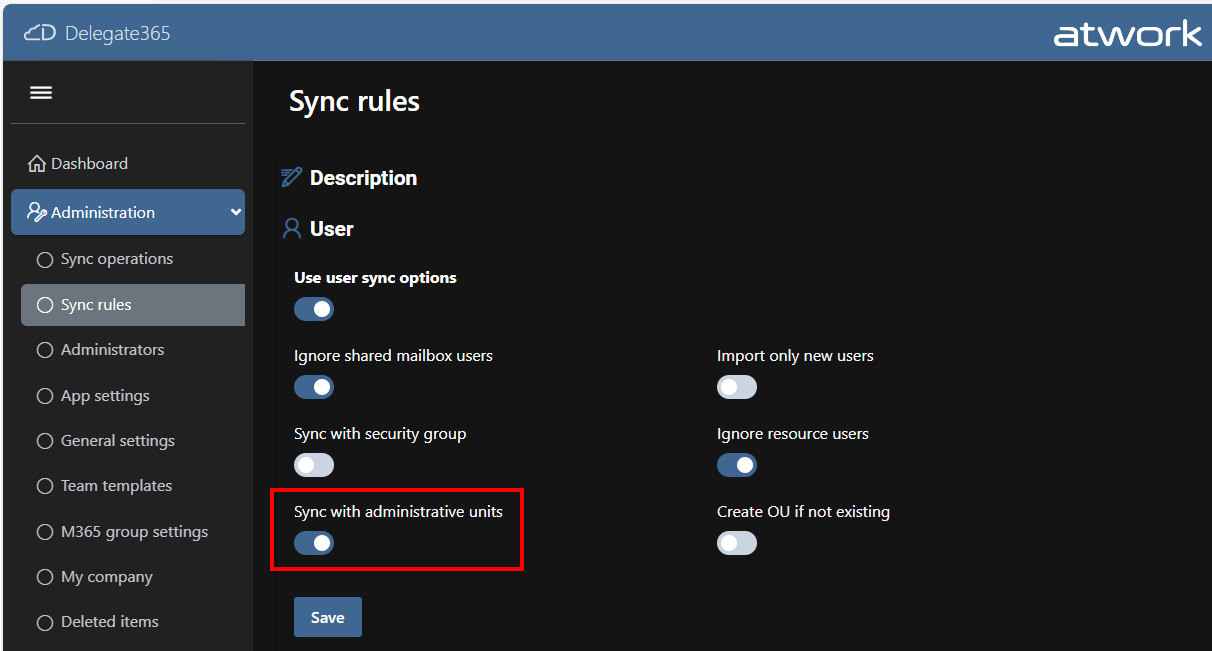
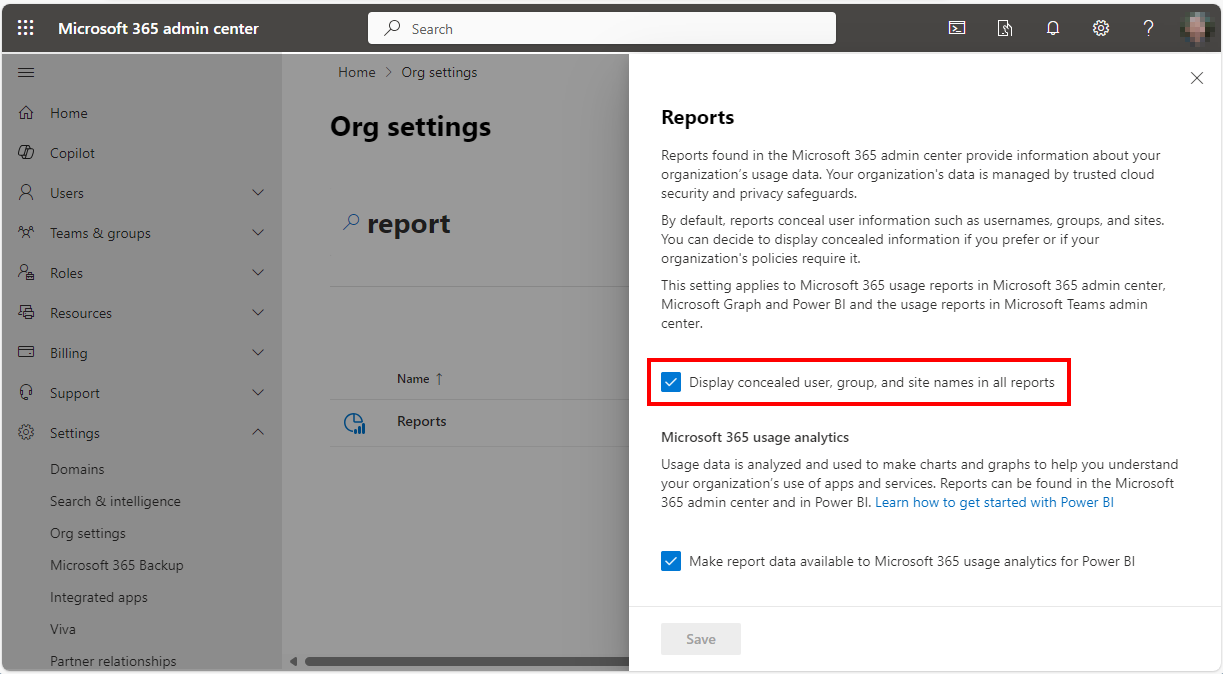
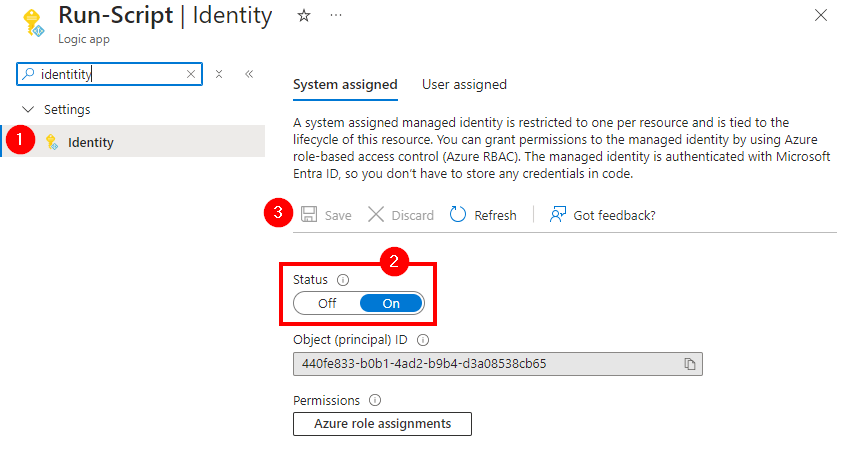
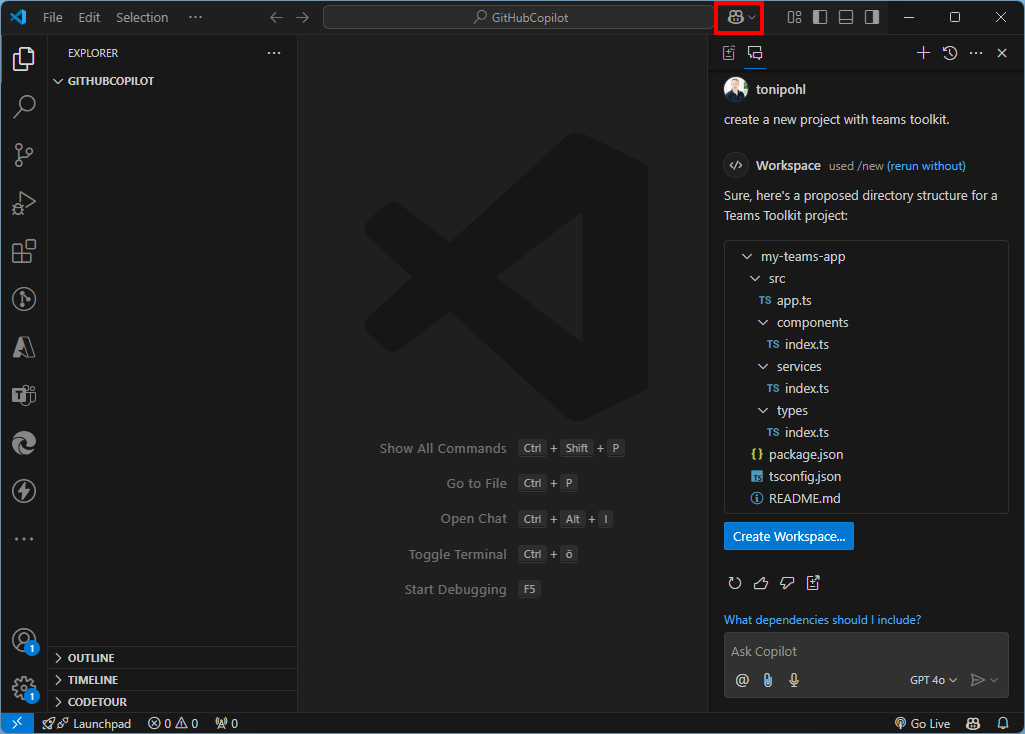
Delegate365 is a powerful web-based solution for managing Microsoft 365 tenants, offering a range of features designed to streamline user, group, license management, and more resource management. Both Delegate365 versions are identical in their core features, but v10 includes some improvements and will be continued. Upgrade soon! Key Features of Delegate365 Both versions of Delegate365 offer a robust set of features, including: User and License Management: Manage users, licenses, and groups within defined organizational units (OUs). Device Management: Assign and manage Devices based on their Tags Group Management: Manage all types of groups, including security, distribution, Microsoft 365, and dynamic groups. Delegation and Automation: Delegate administrative tasks and automate processes to improve efficiency. Auditing and Reporting: Comprehensive logging and reporting capabilities to ensure compliance and provide insights. Mailbox Management: Set mailbox delegations, convert to shared or resource mailboxes, and run message traces. SharePoint and Teams Management: Provision and manage SharePoint sites, Teams tabs, and channels. PowerShell Module: Available for entitled admins to perform operations via PowerShell, with all actions logged. ## Improvements in Delegate365 v10 Version 10 of Delegate365 introduces several enhancements that build on the existing features of v9: ...