Part of the job of Microsoft 365 administrators is to ensure that their users can access and work with all services. This also includes ensuring that applications work. Microsoft Entra manages applications and the associated settings in a central location. It is relevant to know when application certificates and secrets expire in order to renew them in a timely manner. This article shows how you can query which applications need to be updated.
A sample app
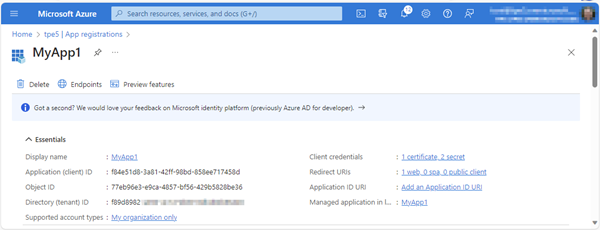
To demonstrate this task with a sample, we create a new app MyApp1 in the Azure portal. We add a redirect URL, a certificate, 2 secrets, and some more app properties, as here.
Get all apps
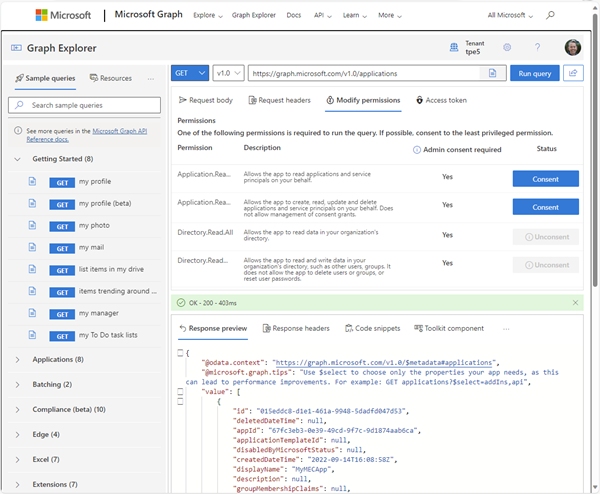
We can use the Microsoft Graph API to get a list of all registered apps in the M365 tenant. Graph Explorer helps to try it out. The screenshot shows the request, and the required permissions.
https://graph.microsoft.com/v1.0/applications
Get secrets and certificates expiration date of one app
We can now use the appId of an application, and ask for the application properties, as the article Get application describes. For our sample MyApp1, we use the appId from above with the following request and syntax:
https://graph.microsoft.com/v1.0/applications(appId='<appid>')
The result shows a bunch of application properties. Relevant for use are the following properties that deliver an array []:
- keyCredentials = certificates
- passwordCredentials = secrets
- requiredResourceAccess = permissions
As always, we should use the $select method to reduce the result and to select only the relevant data in real world. We should append the select query as here:
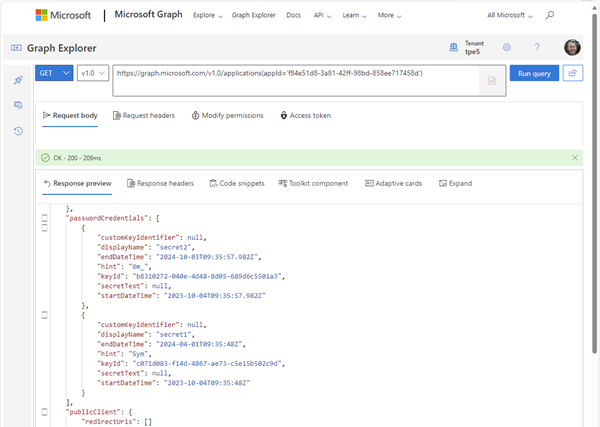
https://graph.microsoft.com/v1.0/applications('<appI>')?$select=displayName,keyCredentials,passwordCredentials We see the endDateTime per secret and certificate.
…
"keyCredentials": [
{
"customKeyIdentifier": "A514FDD0E21511E055C457FE44C62B40DFB3F508",
"displayName": "my personal certificate",
"endDateTime": "2026-05-30T21:33:32Z",
"key": null,
"keyId": "59364f3d-c7a2-467e-b402-a9cd57af4478",
"startDateTime": "2023-05-30T21:23:32Z",
"type": "AsymmetricX509Cert",
"usage": "Verify"
}
],
…
"passwordCredentials": [
{
"customKeyIdentifier": null,
"displayName": "secret2",
"endDateTime": "2024-10-03T09:35:57.982Z",
"hint": "6m_",
"keyId": "b8310272-040e-4d48-8d05-689d6c5501a3",
"secretText": null,
"startDateTime": "2023-10-04T09:35:57.982Z"
},
{
"customKeyIdentifier": null,
"displayName": "secret1",
"endDateTime": "2024-04-01T09:35:48Z",
"hint": "Sym",
"keyId": "c071d083-f14d-4867-ae73-c5e15b502c9d",
"secretText": null,
"startDateTime": "2023-10-04T09:35:48Z"
}
],
…
Here we get secret1, secret2, and the my personal certificate with their end dates, and eventually more application properties if needed. The date and time at which the password expires represented using ISO 8601 format and is always in UTC time, see more here.
With this information we can automate the task and send notifications when the expiration date is in the near future, e.g. alert admins 30 days before expiry.
This functionality will also be part of our Governance Toolkit 365 (GT365) in the next version. Stay tuned with many updates coming with customizable solutions of GT365 and check it out!
Application management can be done and automated with the help of Graph.
Categories: App, Azure, Cloud, Developer, English, Graph, Microsoft, Microsoft365, Security, Tools
Source: https://blog.atwork.at/post/get-application-expiration-dates