Sometimes being a guest in Microsoft Entra tenants feel like Hotel California:
“You can check-out any time you like, but you can never leave!”
It is this time of the year, where people get new phones and this comes also with some necessary cleanup task if you move from one phone to another. While the technology is really awesome today – connect old phone with new phone and transfers happen magically, there are some things that need to be done manually. Things like your Bank account access, cryptocurrency wallets, wallets, digital ID’s and last but not least – your multifactor settings.
I take those phone changing events also to fresh up my tenant memberships. My profession requires me to be an external user in many tenants. My first step – if I am invited to a new tenant, is always to setup MFA. MFA is the most important basic security setting you should do on ALL of your digital accounts as it prevents most security attacks that come with leaked credentials. If it is your private social media account – or your Microsoft Entra account, do yourself a favor and setup MFA on those accounts.
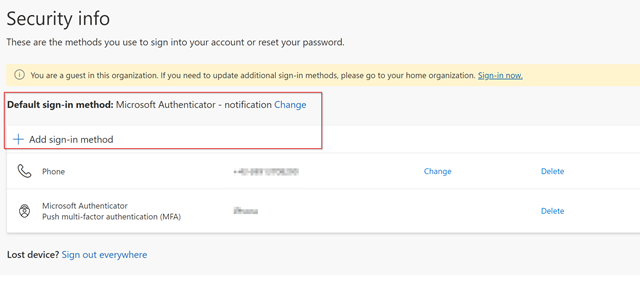
The userflow for refreshing your MFA credentials requires you to update your authenticator app with the new phone. This can be done very easily with https://aka.ms/mfasetup which redirects you to My Sign-Ins | Security Info | Microsoft.com. From here, you are able to update your authenticator app. Some lessons learned over the past years for this:
- always provide more than only ONE MFA method. As much as I want to get rid of Phone Notifications, sometimes this might be the only option for you to get access.
- After you updated your authenticator app – remove the previous one.
- Don’t stay in a tenant for historical reasons – leave if there is time to leave.
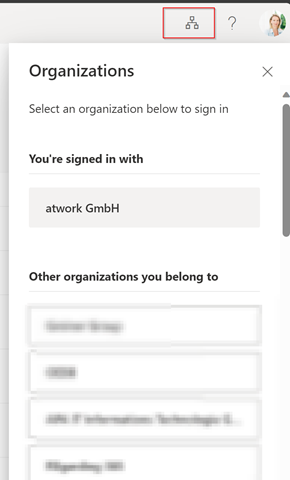
Normally this requires time – but is doable. Just sign in to My Sign-Ins | Security Info | Microsoft.com and afterwards switch to the organization you want to refresh.
Select one of the organizations you belong to and you will be directed to the sign-in page. If you already configured MFA you will be asked (on your old phone) to authenticate and after that you can add the new authentication phone. Everything works and you can update your authentication methods.
Sometimes, the User flow breaks.
There are a couple of reasons, why revalidation does not work for guest accounts. One of the main reasons I see is, that an administrator in the guest tenant blocked your guest user to sign in into the tenant. While there might be reasons to do that short time, this is not a good strategy in long term, for the following reasons:
- the guest account cannot update their authentication methods. So – even when an administrator unblocks you you might be unable to sign in again, because you simply don’t have the original MFA authenticator phone available
- The guest account cannot leave the guest tenant – even after years there are some Zombie accounts left in a tenant due to that.
- The administrator of the tenant has additional – unnecessary work – if he has to reset the MFA authentication flow for the guest – just to let him leave.
- The user acceptance and experience is a very low one
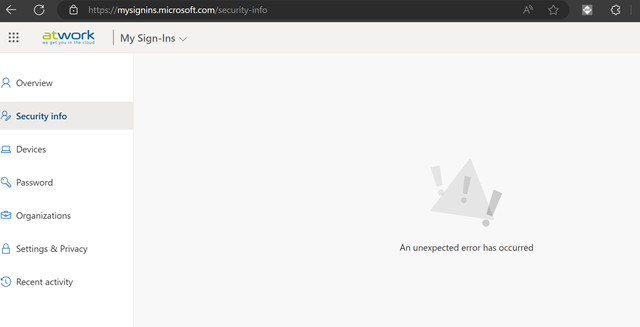
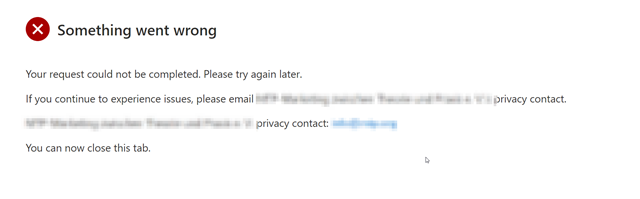
How does that look like? When you try to update the MFA method (not knowing that you were blocked from sign-in) you follow above process and switch to the tenant to update your sign-ins or leave the tenant. Unfortunately the security info presents an unknown error.
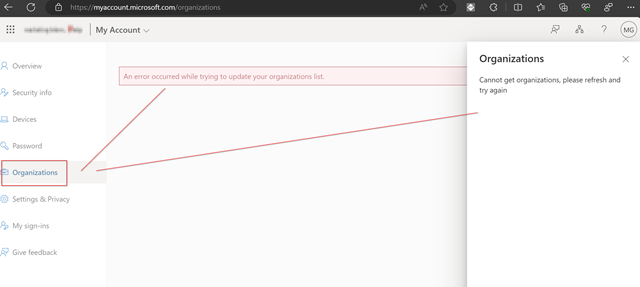
After that – you try to switch the organization – but both ways (in the menu on the right or in the menu on the left you see no organizations loading).
In that case you can reload your organisations by connecting back to your home tenant (or any other that works. Use this URL to connect back (replace CONTOSO with the name of your tenant).
https://myaccount.microsoft.com?tenantId=CONTOSO.onmicrosoft.com
of course – if you know the Tenant ID you can use that as well.
https://myaccount.microsoft.com?tenantId=12345678901234567890
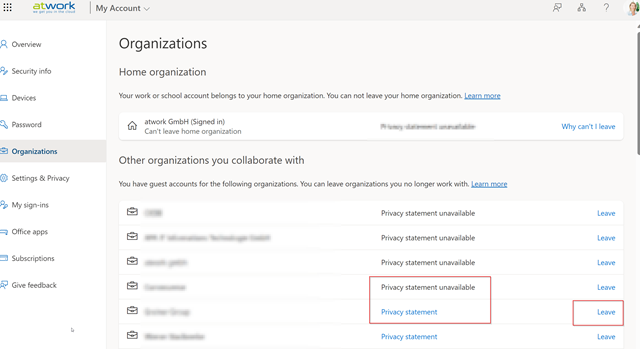
So – what other options do you have to update this information? if you want to sign into that tenant you will need someone of the guest tenant to support you. Another option might be that you try to leave the tenant. To leave an organization you go back to organizations and click on leave.
Unfortunately, if your account was blocked by an adminsitrator this is a dead end as well. You cant update your security info and you can’t leave. Your guest identity will remain locked as a Zombie account in this tenant. If the guest tenant has a setup privacy account, you can try to contact this and get unblocked, before you finally leave.
Please let your guest users leave
As an administrator in a tenant you have a couple of options to support users with self-service. Our recommended approach is to use a governance practice that uses access reviews within Microsoft Entra or our policies provided by Governance Toolkit 365 that allows people to review guests in their tenant. With that method only necessary guests are part of your Teams or Microsoft 365 groups. With that policy in place guests are removed. We have a second policy in place that monitors for guest accounts who have not signed in for X days or which have not accepted the invitation. We remove those accounts on a regular basis.
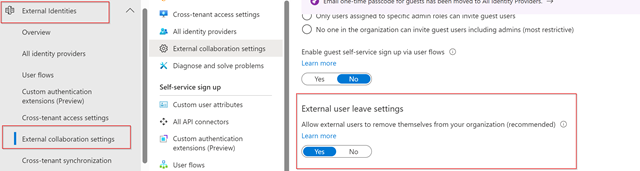
Within Microsoft Entra you can also setup External user leave settings. A prerequisite for this is that you also configure your privacy settings.
This is a good approach and helps administrators having less work and users more self-service.
Categories: Entra, Azure, Governance